The perpetrator As a result had to either have obtained access to the accounts, for instance as a result of hacking, or spoofed them to produce the looks that the email messages came from your ministry, a number of cybersecurity experts told The Epoch Times.This Internet site is not affiliated with any box Office environment or venue This Site is i
 Mr. T Then & Now!
Mr. T Then & Now!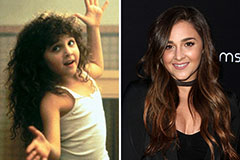 Alisan Porter Then & Now!
Alisan Porter Then & Now!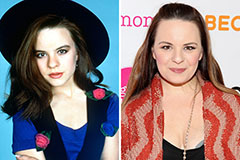 Jenna Von Oy Then & Now!
Jenna Von Oy Then & Now! Mike Vitar Then & Now!
Mike Vitar Then & Now! David Faustino Then & Now!
David Faustino Then & Now!